OpenVPN is one of the most popular and widely used open source software application that implements virtual private network (VPN) technologies for creating secure point-to-point or site-to-site connections in routed or bridged configurations and remote access facilities. It uses a custom security protocol that utilizes SSL/TLS for key exchange.
The purpose of OpenVPN is simple; it allows connecting to other devices within one secure network. It allows to keep online data safe by tunneling them through encrypted servers. So if you’re looking for a reliable, easy-to-use system that is adaptable enough to deal with any operating system, then OpenVPN is a no-brainer.
System Preparation
We are going to setup OpenVPN on the base operating system of Ubuntu Server 14.04. Let’s prepare the base environment before the startup of OpenVPN installation. The only prerequisite is that you have installed Ubuntu 14.04 Operating System and you have sufficient root level privileges for performing general maintenance on your server.
Update your system to refresh the local repository database with the command below.
root@ubuntu-14:~# apt-get update
If you are using an old version of your operating system and need to upgrade all of your installed packages with Operating system, then run the command below.
root@ubuntu-14:~# apt-get upgrade
OpenVPN and RSA Installation
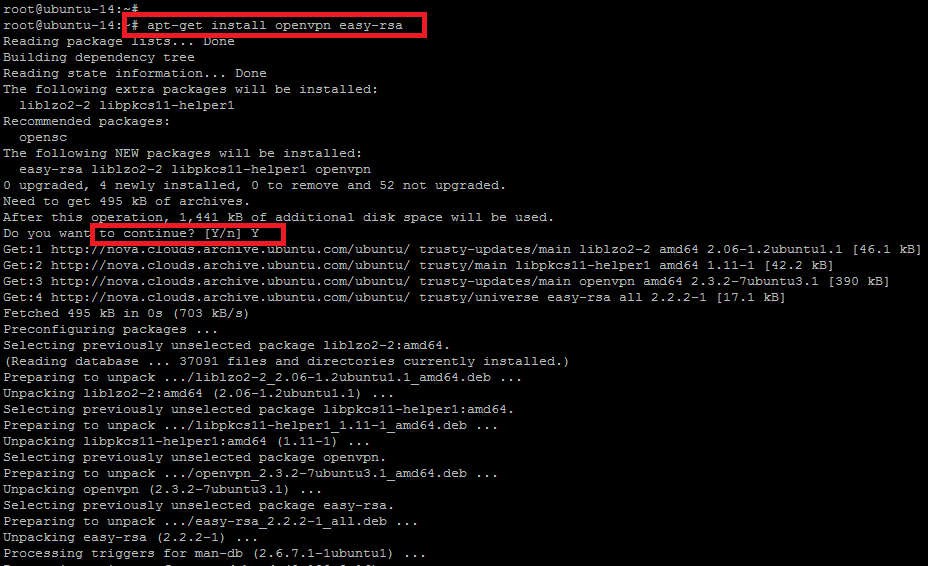
Once your system is updated with the latest updates then install Open VPN and Easy-RSA by running the following command with root user.
root@ubuntu-14:~# apt-get install openvpn easy-rsa
The command will install the new packages with its dependencies. Before the installation process starts, you will be asked to confirm the installation process by typing `Y` for yes and `N` for no.
OpenVPN Server Configuration
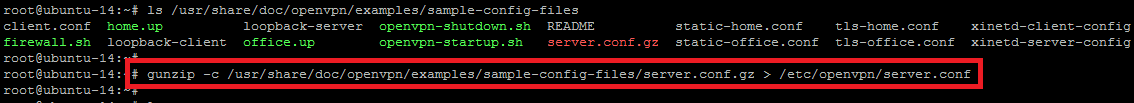
There are some sample VPN server configuration files that can be extracted to `/etc/openvpn` folder for further usage. Now, point to the directory where these example VPN configurations are placed and extract the archive into the required directory with below command.
root@ubuntu-14:~# gunzip -c /usr/share/doc/openvpn/examples/sample-config-files/server.conf.gz > /etc/openvpn/server.conf
Now, to configure its configuration parameters in the `server.conf` file, open with any editor and do the required changes.
root@ubuntu-14:~# vim /etc/openvpn/server.conf
To configure the `Diffie Hellman parameters` in the configurations file, we will update its value to double the RSA key length used when generating server and client keys.
#dh dh1024.pem dh dh2048.pem
To configure the parameters so that the VPN server can pass in the client’s web traffic to its destination, we will uncomment the below line in `server.conf` file.
;push "redirect-gateway def1 bypass-dhcp" push "redirect-gateway def1 bypass-dhcp"
To configure the Public DNS servers provided by opendns.com, uncomment the two line under this section that looks like this.
push "dhcp-option DNS 208.67.222.222" push "dhcp-option DNS 208.67.220.220"
OpenDNS is the default DNS resolvers used by OpenVPN, we can also use whichever DNS service we want to use. Once the necessary parameters have been configured, save the changes and close the file with `:wq!` in case you are using vim editor.
Setup the Certificate Authority
We are going to setup certificate authority that allows your server to generate public and private certificates for other computers. This is one the most important step to setup encrypted communication between the different computers. We will use Easy RSA’s scripts and copy the Easy-RSA generation scripts into the `openvpn` directory.
root@ubuntu-14:~# cp -r /usr/share/easy-rsa/ /etc/openvpn
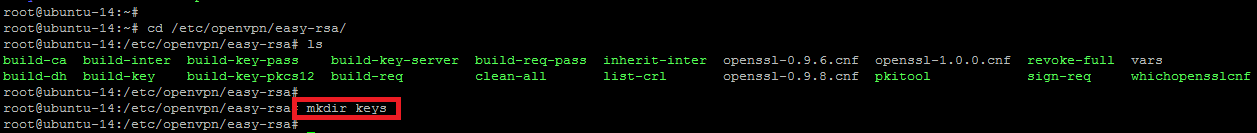
If you list the easy-rsa directory, you will see its different certificate files and directories. Under the easy-rsa directory, we will make a new key storage directory.
root@ubuntu-14:~#mkdir /etc/openvpn/easy-rsa/keys
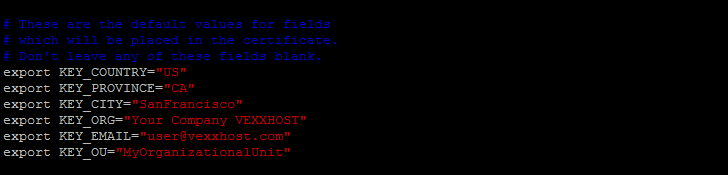
Next, edit `/etc/openvpn/easy-rsa/vars` adjusting the information to your environment, this information is copied to the certificates and keys, and will help identify the keys later.
root@ubuntu-14:/etc/openvpn/easy-rsa# vim vars
# X509 Subject Field export KEY_NAME="EasyRSA"
The variables shown in red should be updated according to your own environment. You would also need to update the OpenVPN configuration files that reference to `server.crt` and `server.key` according to your `KEY_NAME` Otherwise, openvpn service will not start.
root@ubuntu-14:/etc/openvpn# vim server.conf #cert server.crt cert EasyRSA.crt #key server.key # This file should be kept secret key EasyRSA.key
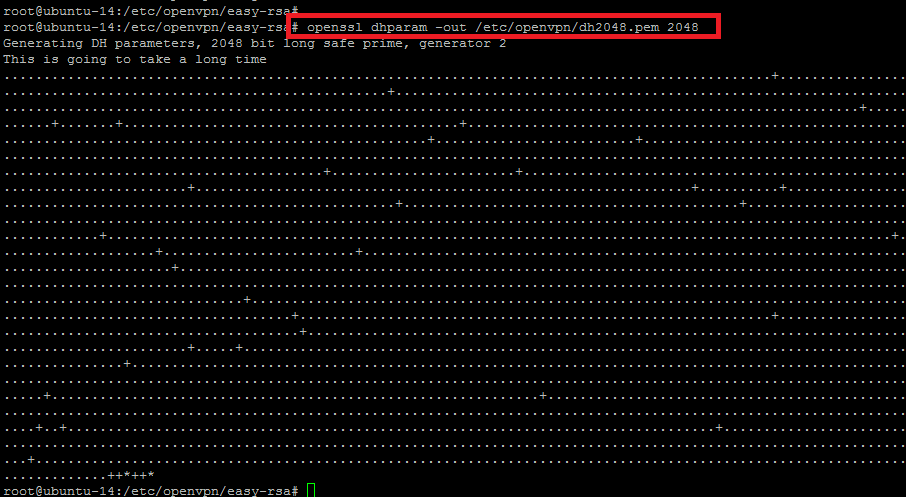
Now we are going to generate the Diffie-Hellman parameters by executing the below command. It might take a few minutes to complete the process.
root@ubuntu-14:/etc/openvpn/easy-rsa# openssl dhparam -out /etc/openvpn/dh2048.pem 2048
Now, initialize the PKI (Public Key Infrastructure) by running the below command within the same directory we are working on.
root@ubuntu-14:/etc/openvpn/easy-rsa# source ./vars
The above command ends up by showing the output like:
NOTE: If you run ./clean-all, I will be doing a rm -rf on /etc/openvpn/easy-rsa/keys
We’ll clear the working directory of any possible old or test keys to make way for the new ones by executing the below command.
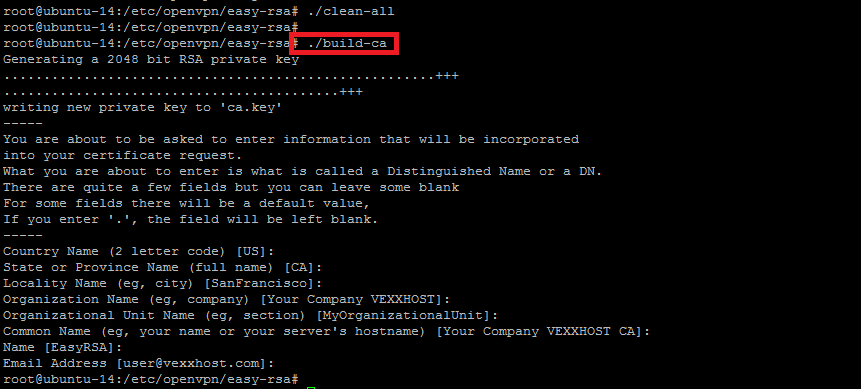
root@ubuntu-14:/etc/openvpn/easy-rsa# ./clean-all
Now we build the certificate authority (CA) by invoking an interactive OpenSSL command. You can accept the default settings at the prompt as we have already configured in the previous steps so simply press `enter` to configure each of the option. If you need to update any of the option then you can also update the settings from here.
root@ubuntu-14:/etc/openvpn/easy-rsa# ./build-ca
Creating Server Certificate
Now, we are going to set up the public and private keys for the actual server. This allows the server to set up its end of the encrypted tunnel between itself and any other computer.
root@ubuntu-14:/etc/openvpn/easy-rsa# ./build-key-server EasyRSA
So working in the same directory, we entered the command to build the server’s key with its export key name as we configured earlier.
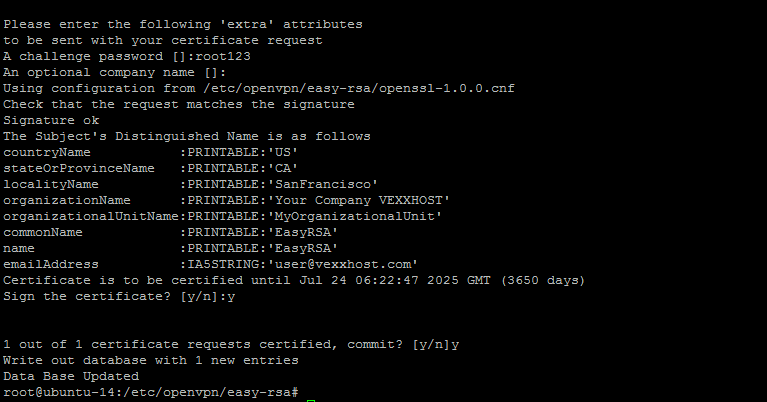
This will be generating a 2048 bit RSA private key where we will be asked to enter the information that will be incorporated into your certificate request.
In addition to the similar options that we had already configured previously, you will be asked to enter some extra attributes as shown.
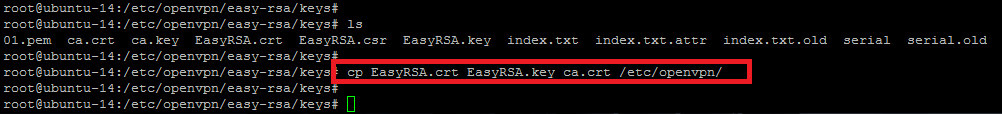
So, we had successfully created the new certificates for the server, now we have to copy these certificates into the `/etc/openvpn` directory.
root@ubuntu-14:/etc/openvpn/easy-rsa/keys# cp EasyRSA.crt EasyRSA.key ca.crt /etc/openvpn/
Start OpenVPN Server
At this point, we are now ready to start openvpn services to check the status of OpenVPN server. Let’s run the following commands to start and check the status of OpenVPN server.
root@ubuntu-14:/etc/openvpn# service openvpn start root@ubuntu-14:/etc/openvpn# service openvpn status
Here is the snapshot with the running status of openvpn server service.
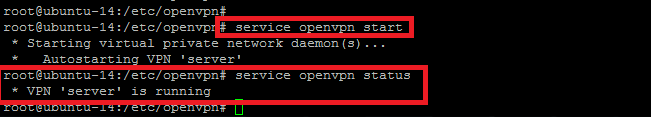
The output shows that we have successfully installed and configured an operation openvpn server. Now in the next steps we will show you about its client setup.
OpenVPN Client Configurations
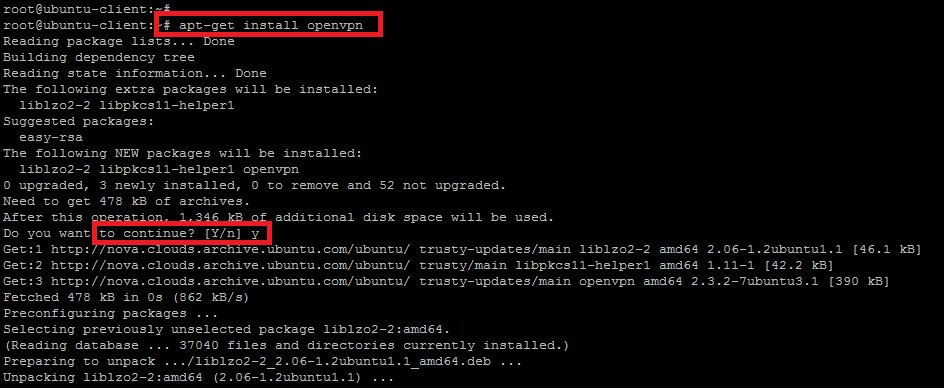
We are going to setup openvpn client that will be used to connect to the openvpn server, so we are starting with its package installation on the client machine which is also running with Ubuntu 14.04 operating system.
Use the following command to start the installation of OpenVPN as shown.
root@ubuntu-client:~# apt-get install openvpn
Now copy the `client.conf` file from the openvpn example files into the `/etc/openvpn/` directory of your openvpn client host.
root@ubuntu-client:~# cp /usr/share/doc/openvpn/examples/sample-config-files/client.conf /etc/openvpn/
You can repeat this section for the new clients by replacing the name of each device with the appropriate client name.
OpenVPN Client Key and Certs Building
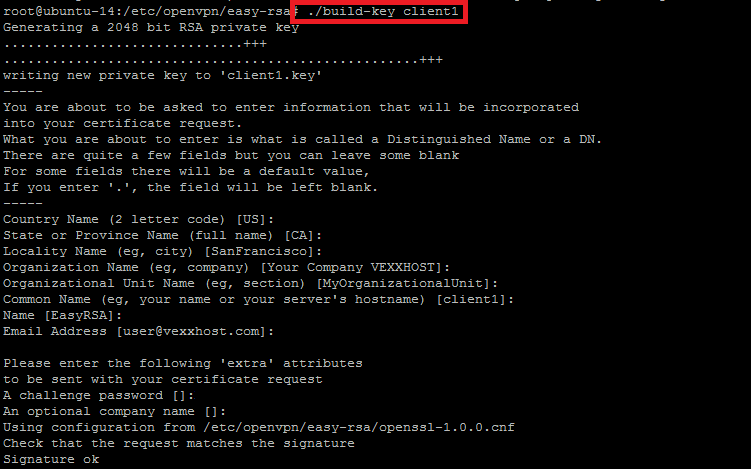
As we did for OpenVPN servers key and certificates building, we will repeat the step for the new client certificates and keys generation. So, to create separate authentication credentials for each device that we want to connect to the VPN, we will have to generate the new certificates with its separate name.
root@ubuntu-14:/etc/openvpn/easy-rsa# ./build-key client1
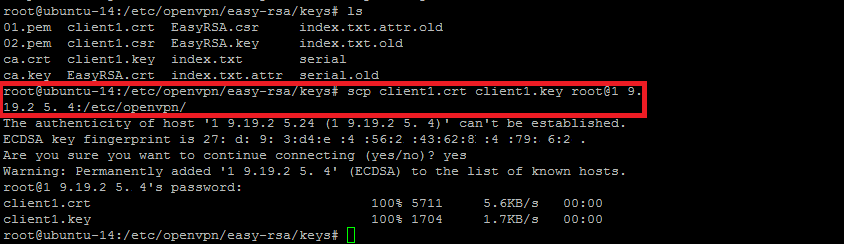
Transferring Certs and Keys to Client Device
Now we need to transfer the client certificate, key, and profile template files to a folder on our client device.
You can also use the below `scp` command to import the files from your server to client machine by giving the source path and destination path.
root@ubuntu-14:/etc/openvpn/easy-rsa/keys# scp client1.crt client1.key
root@xx.xx.xx.xx:/etc/openvpn/
Let’s do some configuration changes in the `client.conf` with the correct certs and keys name as following.
root@ubuntu-client:/etc/openvpn# vim client.conf ca ca.crt cert client1.crt key client1.key
Also change the following line with openvpn’s hostname or IP address with port to connect from the client device.
remote xx.xx.xx.xx 1194
Now, save the changes with `:wq!` and start `openvpn` service on client device.
root@ubuntu-client:/etc/openvpn# service openvpn start
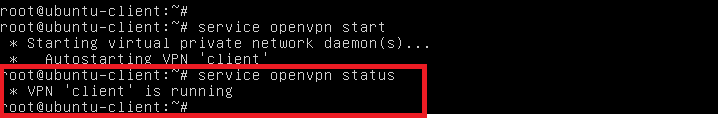
You should see in your ifconfig that a `tun` interface appeared.
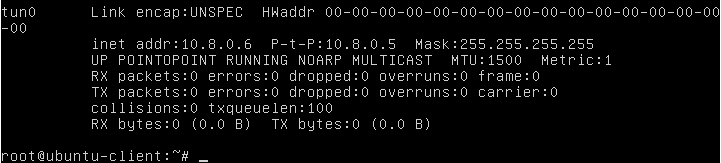
Similarly, if you check in openvpn server side, there will also be a new `tun0` interface present.
Firewall Rules to Connect VPN Server
In order to allow the VPN client to connect to machines behind the VPN server, we must add a couple of routes to the server. First, you’ll want to enable IP forwarding by running the following command.
root@ubuntu-14:~# sysctl -w net.ipv4.ip_forward=1 root@ubuntu-client:~# sysctl -w net.ipv4.ip_forward=1 net.ipv4.ip_forward = 1
Now we only need to make few firewall rules and configuration changes and then re-enable the firewall. So first we will allow the SSH and the port 1194 to both machines with following command.
#ufw allow ssh #ufw allow 1194/udp
Set the default forward policy to ACCEPT, DROP or REJECT by changing this will most likely want to adjust your rules as follow.
root@ubuntu-X:~# vim /etc/default/ufw #DEFAULT_FORWARD_POLICY="DROP" DEFAULT_FORWARD_POLICY="ACCEPT"
Now, we will add some additional `ufw` rules for network address translation and IP masquerading of connected clients by adding some rules in `ufw` `before.rules` file as below.
root@ubuntu-14:~# vim /etc/ufw/before.rules
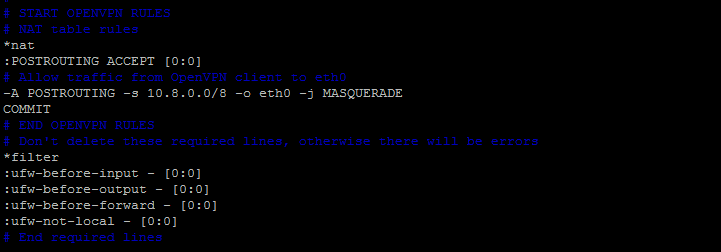
After adding the new rules, enable the `ufw` and then check its status as shown in below. You will be able to see the status of newly added allowed ports.
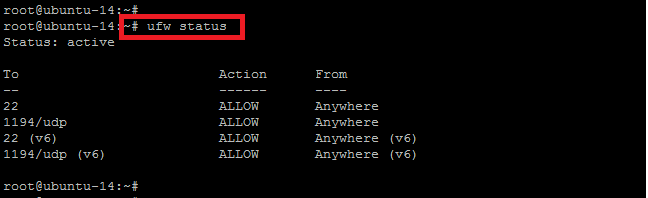
We have almost done the OpenVPN Server and Client setup. Now, finally make sure your routes are working on either your default gateway or your clients. You can use wireshark or tcpdump to check that whether your incoming traffic is fine. You can also manually check the routes on Linux or Windows by issuing the command “route”.
Conclusion
In this detailed article, you have learned about OpenVPN Server and Client setup with installation and configurations using Ubuntu 14.04. You can also install OpenVPN client profiles on the cross platform.